Modern communication networks are inevitably vulnerable to security threats, especially unauthorized access and malicious intrusions. There rises an imperative need to devise robust mechanisms, such as a computerized record system and autonomous authorization, that can secure user-based operations without compromising on the usability and flexibility of network services.
Digital communication networks have grown to serve as the backbone of various services, from online banking to virtual healthcare consultations. These usabilities have made them a primary target for cyber-attacks, leading to breaches, data theft, and unauthorized surveillance. Traditional methods of authentication and authorization have struggled to keep pace with the rapid advancements and diversification of threats, and as a consequence, there is an escalating concern regarding the ability to assure the privacy and security of data as it travels across these networks.
Moreover, the advent of the Internet of Things (IoT) and interconnected smart devices have further compounded the challenge.
Addressing Challenges in Contemporary Digital Autonomous Authorization Practices
Inadequacy of Traditional Authorization Mechanisms
Traditional methods such as passwords, security tokens, and biometrics, while having served their purpose in the past, are increasingly becoming inadequate. They often fall prey to phishing attacks, credential stuffing, and brute force attempts.
Scalability Concerns
With the constant expansion of the digital universe, especially with the incorporation of IoT, it becomes difficult to scale conventional authorization practices. This, in turn, can lead to points of vulnerability, where security measures might be weaker or non-existent.
User Experience Dilemma
It is a challenging task to strike a balance between security and usability. Overly complex security can push users away, while weak security risks threats.
Innovative Approaches to Enhance Digital Authorization with a Computerized Record System
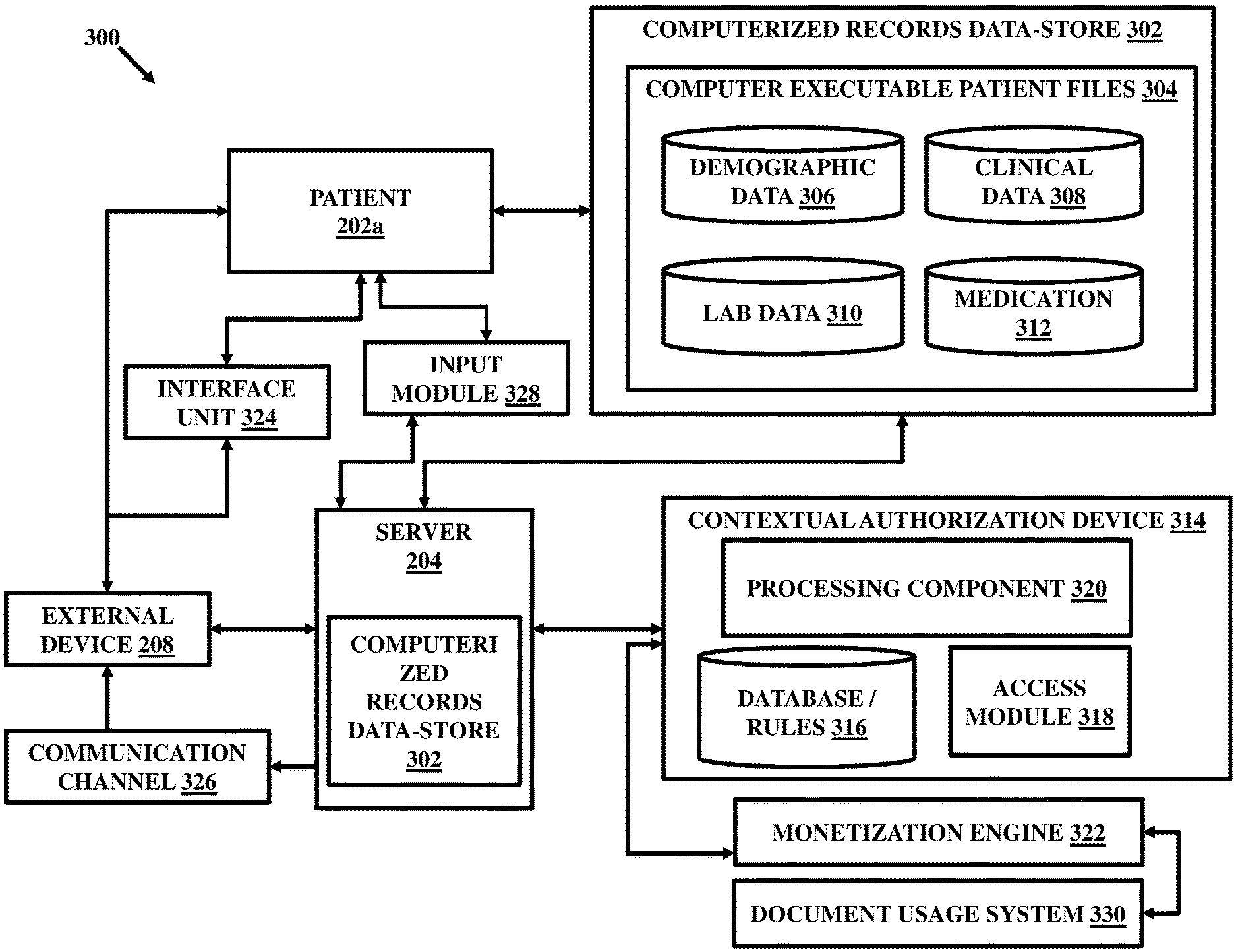
Figure 1
Self-Controlled Digital Authorization Protocols
This technology fine-tunes authorization measures, ensuring enhanced security. It learns and responds to user habits, mitigating potential unauthorized access.
Decentralized Authentication Models
Through the utilization of decentralized technology principles, security is bolstered by dispersing authentication processes. This ensures heightened resilience against potential breaches, preserving the sanctity of the entire communication network.
Continuous Authentication
Restructuring the traditional authentication methods, continuous authentication scrutinizes user activity consistently during sessions. It responds immediately to unusual patterns, enforcing additional verifications to confirm the legitimacy of the user.
Unified Digital Identity Verification
Implementing a centralized methodology, this technology simplifies user experiences by cross-referencing digital identities with diverse metrics. It alleviates the hassle of managing numerous credentials and promotes consistency in user data.
Adaptive Geo-Location Based Digital Authorization
By utilizing geo-specific data, this technology determines access permissions, offering a fluid and dynamic model of authorization. The specific geographical position plays a pivotal role in deciding the type and level of accessibility.
Single-Click Menu Options
This feature provides users with straightforward options for device authorization and it streamlines the authorization process, emphasizing intuitiveness and efficiency.
Variable Access Rights
Adapting to location-based parameters, the technology customizes access rights, ranging from full approval to selective limitations. Such adaptability ensures tailor-made authorization that resonates with the context.
Seamless Communication Protocols
Ensuring optimal performance during the authorization process is achieved by maintaining strong and continuous connections between devices.
Adaptable Authorization with Location Types
This technology harmonizes with location data having pre-set rules, achieving unparalleled accuracy in granting access. Whether based on explicit geographical data or user-defined locations, this method guarantees precise access control. The landscape of digital authorization is undergoing transformative shifts. Emphasizing adaptability, user experience, and dynamic context-aware mechanisms, these innovative methods epitomize the next generation of access security. The continuous evolution and integration of factors like geo-location data and bespoke rules ensure that digital authorization remains both robust and flexible in an ever-changing digital age.
